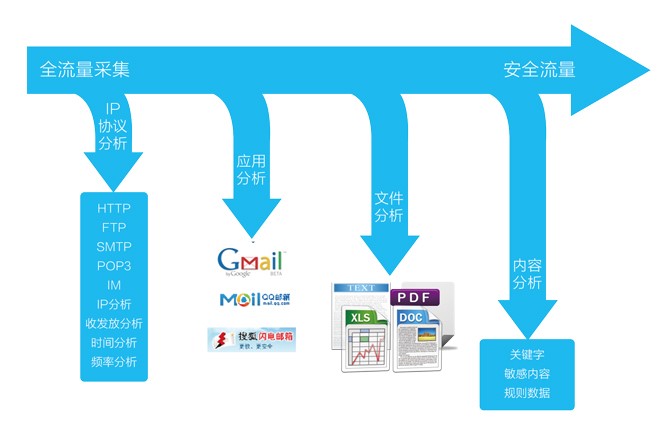
Network sensitive data audit products can mirror the data on network data monitoring, through the network protocol for data reduction and analysis, access to sensitive data in this protocol, the security event log for illegal content, and analyzed the data statistics and the illegal situation.
Core function:
In order to check the bypass mode of network communication, and for all network protocols and the type of content, to determine whether they contain sensitive information before leaving the network information, so that the organization quantified and defined the risk of data loss. By analyzing the bypass mirror data, we can identify sensitive information, output event statistics and situation analysis.
Product characteristics:
1.simple deployment, mature products, high stability
The network sensitive data audit system is deployed in the network node by the bypass mode, without changing the network topology, without interfering with the user's normal business practices.
2.network protocol processing capability is powerful
The protocol processing engine of the network sensitive data audit system can deal with all kinds of network protocols efficiently and cover the network application protocols that most of the users may leak. Especially for domestic users to use network applications to achieve key and timely agreement update, to ensure protection effect.
3.strong data analysis skills
The data analysis engine with independent intellectual property rights of the Esai data analysis algorithm, can find a variety of deep sensitive data. The data analysis engine has been in the public opinion, network monitoring, data analysis and other fields of application for many years, with high efficiency and precision.
4. full event traceability capability
Careful design of security event management, from different dimensions to view event information, provide a variety of statistical analysis reports, comprehensive audit of the incident, to ensure that grasp the dynamics of enterprise data leakage.
Deployment plan: